Mobile networks are dominant in the age of communication and are used to relay mobile communication signals to Public Switched Telephone Networks (PSTN). There is a lot of information that is exchanged on a daily basis. But is your mobile network confidential?
Your mobile phone can be used for industrial espionage, unauthorized transfer of data, or for trading secrets of the enterprises. All this is done through interception of mobile signals, voice calls or using your mobile as a bug. You’d be surprised to hear what’s to follow in this article.
We bring you devices, types, and techniques for mobile interception. Sit tight as we prepare you against being a victim of malicious interception practices.
What is mobile interception?
Mobile interception technology is the storage, recording, tracking, and interception of cellular communications like phone calls, internet usage, SMS, etc. This technology is primarily used for gathering intelligence regarding terrorist or criminal activities.
Even though it started out as an ethical technology for security, there are reports about the misuse of the technology doing the rounds.
However, for those concerned about their privacy during calls, using tools like Call Recorder iCall can provide an added layer of security by recording and securely storing conversations.
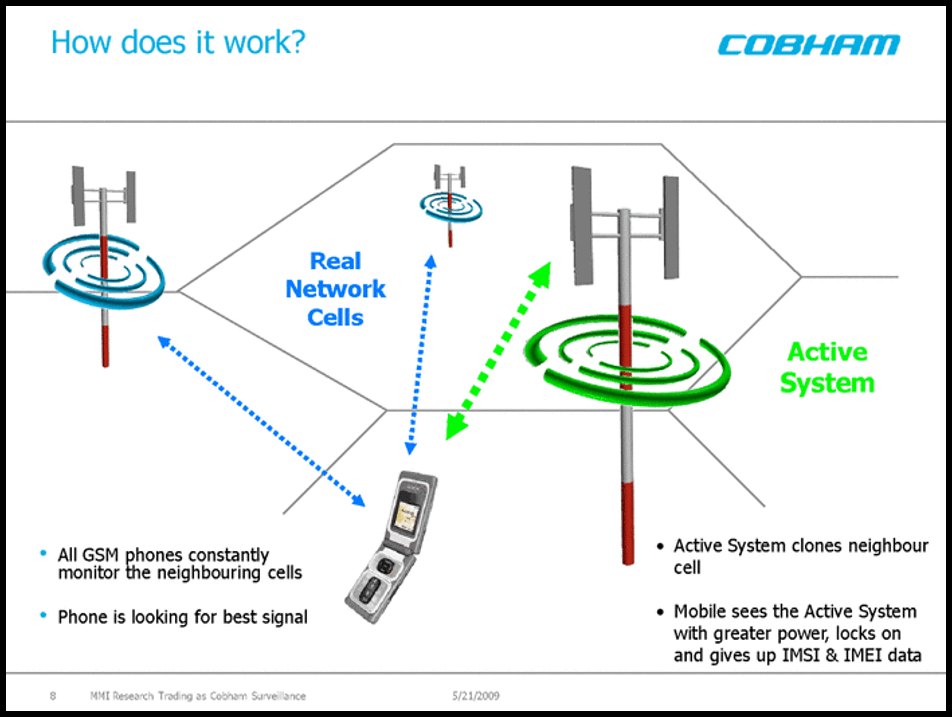
How does mobile interception work?
There are three types of mobile networks – NGN (Next Generation Networks like 3G, 4G, and 5G), GSM (Global System for Mobile communications) and CDMA (Code Division Multiple Access). All three of them are targets of multiple surveillance technologies.
When the mobile phone data travels over these networks, they are passively intercepted between the mobile phone and the base station it is communicating to. Both uplink signal (outgoing voice or data) and downlink (incoming voice or data) signals can be intercepted.
Who can intercept your mobile signal?
Mobile Interception technology is extensively used by law enforcement agencies, military & defense, or authorities like government and federal & local law enforcement agencies (LEAs). These are also termed as Lawful Interceptions. But there are unauthorized intercepts too!
Our expert Sam Tilston from AwesomeResources.co.uk, a professional in cyber security for more than 20 years believes that anyone with a mobile interception device can intercept cellular information like- voice, data transmission, and metadata.
Lawful Interception (LI) – The modern legal interception protocol
Lawful Interception or LI refers to a specific facility in telecommunications where LEA or government with court orders or legal authorization can intercept mobile signals. In common parlance it’s also called selective wiretapping or authorized wiretapping.
Lawful interception is different from the dragnet-type mass surveillance and is usually carried out by intelligence agencies. The data is merely passed through a fiber-optic splice where its extracted and filtered.
Many countries follow local, national, and global standards for lawful interception laid down by ESTI. Governments and authorities require PSPs (Public Service Providers) to install a (LIG) legal interception gateway and LIN (legal interception nodes) for real-time interception.
Lawful Interception architecture
Currently the global standard for Lawful Interception and its architecture is provided by ESTI. The standard architecture in recent use is 3GPP Evolved Packet System (EPS) that provides IP based services.
The ESP architecture attempts to define an extensible and systematic means by which LEAs and network operators can interact. There are three stages in the architecture:
- Collection: target-related call content and data are extracted from these PSP networks.
- Mediation: data is formatted to match the specific standard.
- Delivery: The content and data are delivered to the law enforcement agencies.
Delivery function in the architecture is what is used to hide your sensitive interceptions from Intercepting Control Element (ICE). Even when there are multiple targets on the same number, the authorities have no idea about it.
What is the need for mobile interception?
Apart from the malicious effects like snooping and eavesdropping, mobile interception can be used for security. Want to know the uses?
1. Administration Security
The Administrative function (ADMF) keeps all the intercept activities of individual LEAs separate and interfaces to the intercepting network.
After configuring authorized user access within the network, password protection can be enabled using one of the following security mechanisms:
- CUG/VPN
- COLP
- CLIP
- Authentication & Encryption
The systems or illegal use can be prevented by intercepting the signals in the administrative network.
2. IRI (Intercept Related Information) security
In case of communication failures, IRI can be buffered in the 3G network. After successfully transmitting IRI, the content buffer and total buffer can be deleted via a command or a timer. This prevents the IRI data from being exposed to illegal use.
3. CC (Call Content) security
Data inconsistency, log files, and critically important data like billing information can be suppressed to be viewed by only a fraction of the users over the network. This data can also be deleted after successful transmission to the required personnel.
Can your mobile be intercepted?
If you’re in the crosshairs of the authorities, then chances are that you may be under surveillance right now. Don’t worry, if you’re under one, then you’re not alone!
Lawful interceptions are very common, in fact there are 2000-3000 mobile signals being intercepted and analyzed every day. In fact, if you have a few selected smartphone models from Samsung, chances are that your calls are being intercepted.
The presence of Shannon-branded baseband chips, a tracing IC (integrated circuit) and RF (radio frequency) transceiver make it a device that can be easily intercepted. Calls and messages can be intercepted by creating a proxy base station by frankly anyone with a device.
What is the future of mobile interception market?
The market of mobile interception is estimated at $1.8 billion globally, and $ 226.1 million in the U.S. alone. The market is estimated to grow at a tremendous rate of 5.8% annually for the next decade.
With new developments of communication frequencies, networks and channels, integration with newer interception systems will create a little hurdle. New and portable devices are being deployed every day across the world to hamper the mobile interception market.
In summary
Mobile interception is a debatable topic. On one hand, you are always on someone’s radar and that’s something that you can’t live with knowing. On the other hand, it’s a crucial and apt technology for intercepting malicious calls and threats.
As hard as it may sound, it’s hard to negate the importance of mobile interception, as long as it’s legal, and meets the global standards of lawful interception.
Hey, as long as it continues to save millions of lives by combating increasing criminal activities and security threats, it’s always a handy technology and probably will be in the future too.







Leave a Comment